Welcome
First of all, may I welcome you to my site. My name is Chris and I'm from the UK and work as a Systems Engineer for Cisco. This blog was initially created to post up my subnetting technique but has now got more stuff to do with attaining Cisco certifications. Either way I really hope that the content is sufficent for your needs and I look forward to hearing your feedback. If you find that the content really helps you please feel free to donate using the PayPal link on the right.
To view the index of all my articles please click here.
Complex Route Summarization
Thursday 17 April 2008
I've already posted about route summarization but I found this interesting technique for calculating complex route summaries at http://www.sadikhov.com/forum from member MarkinManchester. Thanks Mark!
Sometimes you are asked to filter a complex set of routes using as few lines as possible. Here we will examine a way to calculate the subnet and wildcard for such a scenario. With some practice, you should be able to calculate any set in 5 minutes or less. It is also recommend to test your results in a lab setting, using loopbacks and distribute-lists.
For example, say we are asked to filter the following routes using a one-line filter:
102.17.63.0
126.22.61.0
111.22.57.0
125.33.101.0
First, make a table as shown:
Then, enter the decimal digits from the first octet in the left-hand column. Convert each number to binary. You can use Windows Calculator set to Scientific Mode to do the conversion if you so wish.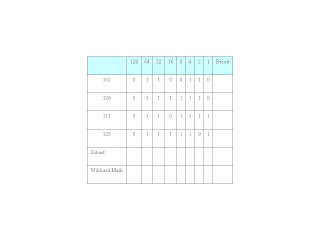
In the binary area, first check the octet then column by column, apply the following rules:
- If the entire octet is 0, the subnet is 0 for that octet, and the mask is 255 for that octet.
- Else If the column is all 0’s, the subnet is 0, and the mask is 0
- Else If the column is all 1’s, the subnet is 1, and the mask is 0
- Else the column is a mixture of 1’s and 0’s, the subnet is 0, and the mask is 1.
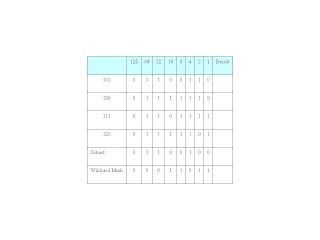
For the first octet the table should look like:
Convert the binary Subnet and Wildcard Mask to decimal to complete the table:
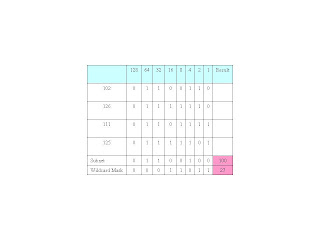
So far, our filter looks like: 100.xxx.xxx.xxx 27.xxx.xxx.xxx
For the second octet the completed table should look like:
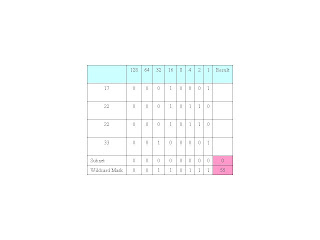
Our summary address now looks like: 100.0.xxx.xxx 27.55.xxx.xxx
For the third octet the completed table should look like:
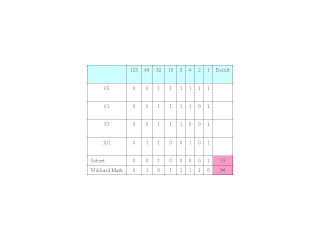
Our summary address now looks like: 100.0.33.xxx 27.55.94.xxx
Now the last octet for all addresses is zero so the subnet address must be 0 in the last octet and the wilcard mask must be 255 in the last octet.
Our completed summary address looks like: 100.0.33.0 27.55.94.255
Apply this technique as you wish, for example:
access-list 1 permit 100.0.33.0 27.55.94.255
This is a great technique for reducing something complex into easier computation so hats off to Mark again for turning me on to this.
Posted byChris Bloomfield at 19:47 5 comments
Labels: complex, Route Summarization, Summarisation, summary routes, Supernetting, wildcard
GNS3 PEMU Configuration Guide - latest version 0.4.1
Thursday 3 April 2008
The latest version of GNS3 (0.4.1) offers:
* A dynamic mode (no design/emulation modes)
* A new .net save/load.
* c1700 and WICS support.
* PIX emulation.
* Dynamips's ATM bridge.
* Capture feature for links from the GUI.
* IDLE PC calculation from the GUI.
* GUI improvements (save the window state when closing GNS3 ...)
* Annotation feature.
* Project feature (you can keep router configs, nvram ...)
* NULL NIO support.
* PDF export.
* New languages.
For those that need to set up GNS3 for the first time, I have amended my GNS3 Configuration Guide based on version 0.3.x so that users of 0.4.x can understand and follow it too.
Anyway, back to the stand-out new feature - PIX emulation, yay! My only minor gripe is that PIX is now EOL but as there are loads of PIX firewalls out there I'm not complaining.
Hopefully you can tell but I'm not the kind of guy to leave people in the lurch and chuck them in the deep end so here is a step-by-step guide on how to configure a PIX firewall in the latest version of GNS3.
1. Download and install the latest version of GNS3 from http://www.gns3.net/download and ensure that you install the PEMU wrapper (this is done by default when installing GNS3).
2. Open up GNS3 and you will see a screen like the following (notice how it has changed from the old version, especially that you run the IOS and console to devices from the one screen).
3. Now go to Edit on the menu bar and select Preferences. You will now see the screen below:
4. Now select the PEMU option from the left-hand menu to be presented with a screen like the one below. All you need to do now is point to the PIX Image where it says "PIX Image". Once you have done that click on Apply, then Close.
5. Now drag and drop a PIX firewall from the left-hand menu of the main screen onto the centre stage. Right-click on the firewall and select Start then Console:
6. You should now see your Console session to your PIX firewall as below:
Posted byChris Bloomfield at 11:26 4 comments
Labels: Cisco, configuration, dynagen, dynamips, firewall, gns3, ios, pemu, pix, router






