Welcome
First of all, may I welcome you to my site. My name is Chris and I'm from the UK and work as a Systems Engineer for Cisco. This blog was initially created to post up my subnetting technique but has now got more stuff to do with attaining Cisco certifications. Either way I really hope that the content is sufficent for your needs and I look forward to hearing your feedback. If you find that the content really helps you please feel free to donate using the PayPal link on the right.
To view the index of all my articles please click here.
GNS3 Configuration Guide
Tuesday, 18 December 2007
What is GNS3 I hear you cry? Well, imho, it is the best tool on the market to practice router configuration without having an actual router in front of you. What sets it apart is that it is a Cisco IOS emulator, not one of those nasty simulators that constrain the commands that can be used. The caveat is that you will need a Cisco IOS, for example I use the 3660 Crypto IOS. I have a support contract with Cisco so I can access an IOS however if you look around enough you will be able to find a Cisco IOS for yourself.
GNS3 is actually the graphical front-end of Dynamips/Dynagen and allows you to drag-and-drop routers onto a stage, connect them up, run IOS on them, and save their configs, just as if you had your own network. It can be a little confusing to set up first of all so I will present a step-by-step guide below of how to install and configure GNS3 including a couple of advanced options which will allow you to run Cisco Security Device Manager (SDM) on your PC.
Installation and Configuration
This process needs to be done only the once.
1. Download GNS3 from here and choose the installer which includes Dynamips, WinPCap and the binary version of GNS3 and install, accepting the various licence agreements etc.
2. You now need a Cisco IOS. Get one from Cisco if you have a CCO account with Support or find an IOS on Google.
3. Now open up GNS3.
Users of GNS3 version 0.5 will see the following: 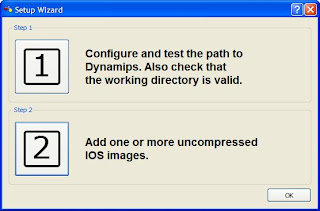
4. Now click on Step 1.
You will see something similar to the following: 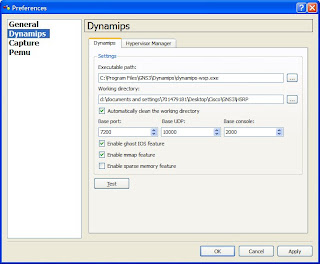
5. The executable path should point to the dynamips-wxp.exe in the Program Files directory. Change the Working Directory to a desired folder then click on the Test button. You should see that Dynamips has successfully started, if so click Apply then OK. If not you should double-check the Executable Path and the Working Directory: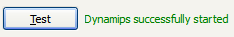
6. Go back to the Setup Wizard and choose Step 2 and you should get a screen similar to below: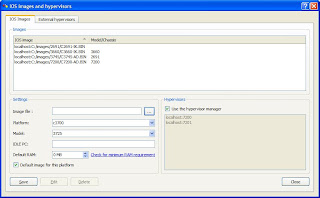
7. In the Settings section you need to point to the IOS image you copied in Step 2 and select the platform and model, then click on Save. The value of the IDLE PC section will be blank and leave blank for now. Now click on Close. Click on OK to close the Setup Wizard.
8. On the main screen drag a router onto the main screen then right-click on it, select Start and wait for the IOS to start and then right-click and select Console. You should now get a DOS screen open up with a telnet session for the router. NOTE: The length of time you have to wait for this to start depends on the speed and memory of your PC. 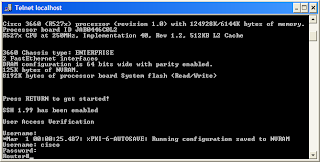
9. Say “No” to initial configuration dialog until you get to the Router> prompt. Now type enable to go into Enable mode.
10. Go back to the GNS3 session KEEPING THE CONSOLE SESSION OPEN.
11. Type idlepc get your-router-name for example idlepc get R0 and wait for some idlepc values to be displayed. Make a note of these values and click Cancel.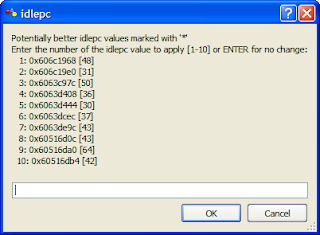
12. By default Dynamips will take up 100% of your CPU usage and you need to specify an idlepc value to get that changed. Close down the console session and open up Task Manager on your PC (usually CTRL-ALT-DELETE) then go to the Performance tab.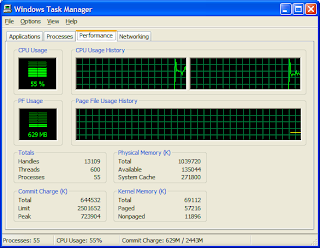
13. Go to Edit-->IOS Images and Hypervisors and select the IOS you identified in Step 4 then click on Edit. Enter the first idlepc value you wrote down from Step 12 then click on Save then Close.
14. Start the IOS again as you did in Step 8 then console to the router. View the CPU utilisation in Task Manager and see if it falls below 5%. If it stays at 100% then go back to step 14 and change the idlepc value to the next one in the list. Repeat this until you get an idlepc value that has the CPU utilisation at around 5% or less.
You have now successfully installed and configured GNS3.
Configuring a Serial Interface on a Router
By default the 3660 image that I use comes with 2 FastEthernet interfaces. In order to simulate WAN links you need to add serial interfaces to the router as outlined below.
1. Right-click on your router, choose Configure, then click on your router name.
2. Click on the slots tab and change slot 1 (or any other slot other than slot 0) to NM-4T. This will provide you with 4 serial interfaces. NOTE THAT THE SLOT NAME MAY BE DIFFERENT DEPENDING ON WHICH IOS YOU USE.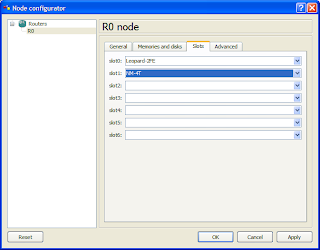
3. Click on Apply then OK.
Adding a switch module to your router
Follow the same steps as you did for configuring a serial interface but choose the NM-16ESW module from the drop-down list.
Connecting two or more routers
You will come to the point where configuring just one router is not sufficient such as when you want to run a routing protocol. The following guidelines show you how to connect routers together.
1. Drag two or more routers onto the stage and configure their slots if required. Display their hostnames by pressing the ABC button on the toolbar if they are not already displayed.
This is a personal preference and allows you to track which router is which.
2. Now click on the interface button on the toolbar and select Manual.
The interface button changes to a red cross.
Now left-click on a router and select an interface which you want a cable connected to. Now click the router to which you want to connect to and select the interface on that router for the other end of the link. You should now see the link has been drawn. Once you have finished configuring the interfaces click the interface button (red cross) to get out of interface configuration mode (the icon will revert to the telephone jack symbol). The picture below shows three routers with a FastEthernet connection and the other with a Serial link (zig-zag line).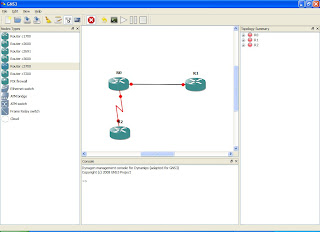
3. Notice that each link has got a red dot on it. When you start the IOS each dot should turn to green which denotes that each router has successfully started the IOS.
Saving your configuration
After all your hard work on the command line you will probably want to save your configuration and reuse it on another day. Follow the steps below to save your work:
1. Go to File-->Save As and save your topology where you want as a .net file. When it comes to reusing this topology just double-click on the .net file to open it up in GNS3.
2. On each router save your config using copy run start
3. Back in GNS3 type save /all in the bottom half of the screen to save all of the configs into the .net file. If you want to save the config of only one router you can replace the keyword all with the name of the router you wish to save the config of. You can also extract the configs by clicking on the "Extract all start-up configs" button on the toolbar.
Configuring a host in the network (Advanced)
There may be an occasion when you want to connect a host in your topology such as running Cisco’s Security Device Manager (use of this may figure in future CCNA exams). To do this you must first configure a Loopback Adapter on your PC.
1. Go to Control Panel-->Add Hardware then click Next
2. Yes I have already connected the hardware
3. Scroll to the bottom and click on Add a new hardware device then Next
4. Install the hardware that I manually select from a list (Advanced)
5. Click on Network Adapters then Next
6. Select Microsoft as the Manufacturer then on Microsoft Loopback Adapter under Network Adapter then click Next then Next again.
7. Open up Control Panel-->Network Connections to see the adapter in place.
Now that you have created a loopback adapter you will want to connect it to a router. To do this, follow these steps:
1. In the GNS3 installation directory run the Network Device List.bat file which will give you the Ethernet address of your Loopback Adapter.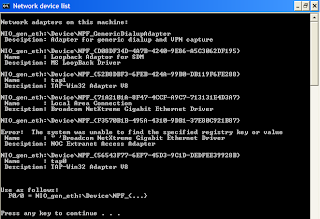
Notice the second adapter shown where description is MS Loopback Driver. I have renamed the adapter as Loopback Adapter for SDM. We are interested in the NIO_gen_eth string.
2. Go into GNS3 and drag a cloud onto the stage.
3. Right-click the cloud and select configure.
4. Choose your cloud from the list.
5. In the Generic Ethernet NIO section select your Loopback Adapter from the drop-down list (the one that matches what is shown in Step 1) and click on Add, Apply, the OK.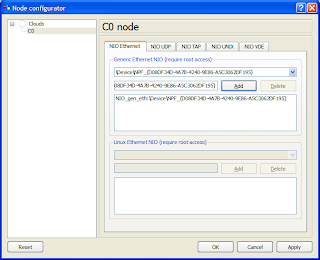
6. Now connect a FastEthernet port on your router to the cloud as you would connect two routers.
7. Configure an IP address and subnet mask on the router interface connected to the cloud and bring the interface up.
8. Go to Control Panel-->Network Connections and right-click your adapter. Choose Properties then Internet Protocol (TCP/IP) and give it an IP address in the same subnet as the router’s FastEthernet interface with the same subnet mask and with a default gateway matching the IP address of the router’s interface.
Example:
Router’s FastEthernet 0/0 interface connected to the cloud:
On the router I would have something like:
Router(config)#int fa0/0
Router(config-if)#ip address 192.168.1.1 255.255.255.0
Router(config-if)#no shut
On the PC I would have something like:
IP address = 192.168.1.2
Subnet Mask = 255.255.255.0
Default Gateway = 192.168.1.1
You should now be able to ping between your PC and the router
Running SDM (Advanced)
There may be a need to practice using the Cisco Security Device Manager (SDM) for your exam and the following steps show you how to configure it.
1. Download and install SDM from the www.cisco.com or from a share on the web.
2. Choose to only install SDM to your PC, NOT to the router.
3. Now configure your router with a hostname and a domain name in order for SSH to work:
Router#conf t
Router(config)#hostname SDMRouter
SDMRouter(config)#ip domain-name SDMDomain
4. Now configure your router with the following commands:
SDMRouter(config)#username your_username privilege 15 secret 5
SDMRouter(config)#ip http server
SDMRouter(config)#ip http secure-server
SDMRouter(config)#ip http authentication local
SDMRouter(config)#line vty 0 4
SDMRouter(config-line)#login local
SDMRouter(config-line)#transport input telnet ssh
SDMRouter(config-line)#privilege level 15
SDMRouter(config-line)#line cons 0
SDMRouter(config-line)#login local
SDMRouter(config-line)#transport input telnet ssh
SDMRouter(config-line)#privilege level 15
SDMRouter(config-line)#exit
SDMRouter(config)#crypto key generate rsa gen mod 1024
5. Now double-click the SDM icon and enter the IP address of the router and tick the box asking about HTTPS then click on Launch.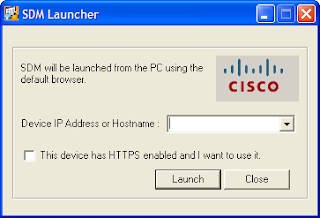
6. Ensure you allow popups on your browser.
7. Enter username and password as defined after step 3.
8. Say yes to allow SDM to install.
You should now have a screen similar to the one below although this may be because I used a username and password of “cisco” which are the default.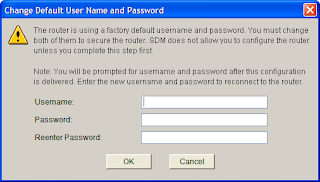
9. Select a new username and password for the router then click OK. You should see the screen below then click OK.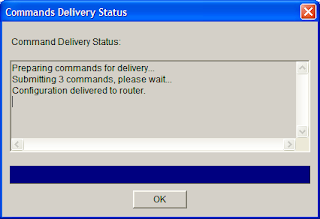
10. You should now be in SDM and able to configure the router.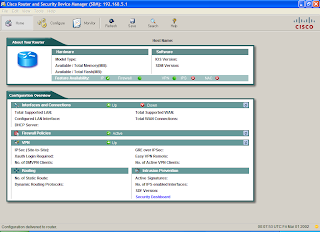
Posted byChris Bloomfield at 09:11 67 comments
Labels: adapter, Cisco, configuration, dynagen, dynamips, emulator, gns3, guide, idlepc, ios, loopback, microsoft, NIO_gen_eth, router, sdm
How to calculate the Wildcard Mask
Wednesday, 12 December 2007
This is really simple.
Simply subtract your mask from 255.255.255.255 to get your wildcard mask.
Example:
The wilcard mask of /26 is:
255.255.255.255 - 255.255.255.192 = 0.0.0.63
The wilcard mask of /19 is:
255.255.255.255 - 255.255.224.0 = 0.0.31.255
The wildcard mask of /12 is:
255.255.255.255 - 255.240.0.0 = 0.15.255.255
There is an alternative way of calculating your wildcard mask which follows on from the Subnetting Made Easy post about boundaries. If you do not understand what I mean about boundaries please read that post.
For example, if you had a /28, your next boundary is /32 so 32 - 28 = 4 and 24 = 16. If we subtract 1 from the block size it gives us 15 which is what we put into our wildcard mask in the octet that we are subnetting in. All octets before the one we are subnetting in are 0 and all octets after the octet we are subnetting in should be 255.
Let's follow that again:
1. /28 gives us 15 in the last octet (i.e. 32 - 28 = 4 and 24 - 1 = 15)
2. All octets before that octet have to be 0 (i.e. 1st, 2nd, and 3rd octets)
3. All octets after that octet have to be 255 (not applicable here as /28 is in the last octet)
4. We therefore have 0.0.0.15 as our wildcard mask
Let's do it with a /21:
1. /21 gives us 7 in the third octet (i.e. 24 - 21 = 3 and 23 - 1 = 7)
2. All octets before that octet have to be 0 (i.e. 1st and 2nd octets)
3. All octets after that octet have to be 255 (i.e. the 4th octet)
4. We therefore have 0.0.7.255 as our wildcard mask
Let's do it with a /9:
1. /9 gives us 127 in the second octet (i.e. 16 - 9 = 7 and 27 - 1 = 127
2. All octets before that octet have to be 0 (i.e. the 1st octet)
3. All octets after that octet have to be 255 (i.e. the 3rd and 4th octet)
4. We therefore have 0.127.255.255 as our wildcard mask
HTH,
Chris
Posted byChris Bloomfield at 11:36 25 comments
Labels: block, mask, size, Subnet, Subnetting, wildcard
VLAN Trunking - Remembering which combination creates a Trunk Link
Thursday, 6 December 2007
Ah, you've probably seen the table and thought to yourself "that doesn't look bad." Well let's make it easier:
1. If one end of the link is configured as an access port then the link will NOT trunk.
2. If BOTH ends of the link are AUTO then the link will NOT trunk
3. If one end is a trunk and the other is auto BUT THE TRUNK PORT IS CONFIGURED FOR NO-NEGOTIATION then the link will NOT trunk.
4. ALL OTHER COMBINATIONS WILL TRUNK
Posted byChris Bloomfield at 14:37 4 comments
Labels: 802.1q, auto, isl, negotiate, non-broadcast, trunk, trunking, vlan, vtp
Subnetting Made Easy - Critically Acclaimed!
Wednesday, 28 November 2007
We need to start with the fundamentals of IP addressing. An IP address is made up of 32 bits, split into 4 octets (oct = 8, yes?). Some bits are reserved for identifying the network and the other bits are left to identify the host.
There are 3 main classes of IP address that we are concerned with.
| Class A | Range 0 - 127 in the first octet (0 and 127 are reserved) |
| Class B | Range 128 - 191 in the first octet |
| Class C | Range 192 - 223 in the first octet |
Below shows you how, for each class, the address is split in terms of network (N) and host (H) portions.
| NNNNNNNN | . | HHHHHHHH | . | HHHHHHHH | . | HHHHHHHH | Class A Address |
| NNNNNNNN | . | NNNNNNNN | . | HHHHHHHH | . | HHHHHHHH | Class B Address |
| NNNNNNNN | . | NNNNNNNN | . | NNNNNNNN | . | HHHHHHHH | Class C Address |
At each dot I like to think that there is a boundary, therefore there are boundaries after bits 8, 16, 24, and 32. This is an important concept to remember.
We will now look at typical questions that you may see on subnetting. More often than not they ask what a host range is for a specific address or which subnet a certain address is located on. I shall run through examples of each, for each class of IP address.
What subnet does 192.168.12.78/29 belong to?
You may wonder where to begin. Well to start with let's find the next boundary of this address.
Our mask is a /29. The next boundary is 32. So 32 - 29 = 3. Now 23 = 8 which gives us our block size.
We have borrowed from the last octet as the 29th bit is in the last octet. We start from zero and count up in our block size. Therefore it follows that the subnets are:-
192.168.12.0
192.168.12.8
192.168.12.16
192.168.12.24
192.168.12.32
192.168.12.40
192.168.12.48
192.168.12.56
192.168.12.64
192.168.12.72
192.168.12.80
.............etc
Our address is 192.168.12.78 so it must sit on the 192.168.12.72 subnet.
What subnet does 172.16.116.4/19 sit on?
Our mask is /19 and our next boundary is 24. Therefore 24 - 19 = 5. The block size is 25 = 32.
We have borrowed into the third octet as bit 19 is in the third octet so we count up our block size in that octet. The subnets are:-
172.16.0.0
172.16.32.0
172.16.64.0
172.16.96.0
172.16.128.0
172.16.160.0
.............etc
Our address is 172.16.116.4 so it must sit on the 172.16.96.0 subnet. Easy eh?
What subnet does 10.34.67.234/12 sit on?
Our mask is 12. Our next boundary is 16. Therefore 16 - 12 = 4. 24 = 16 which gives us our block size.
We have borrowed from the second octet as bit 12 sits in the second octet so we count up the block size in that octet. The subnets are:-
10.0.0.0
10.16.0.0
10.32.0.0
10.48.0.0
.............etc
Our address is 10.34.67.234 which must sit on the 10.32.0.0 subnet.
Hopefully the penny is starting to drop and you are slapping the side of your head realising that you were a fool to think it was hard. We will now change the type of question so that we have to give a particular host range of a subnet.
What is the valid host range of of the 4th subnet of 192.168.10.0/28?
Easy as pie! The block size is 16 since 32 - 28 = 4 and 24 = 16. We need to count up in the block size in the last octet as bit 28 is in the last octet.
192.168.10.0
192.168.10.16
192.168.10.32
192.168.10.48
192.168.10.64
.................etc
Therefore the 4th subnet is 192.168.10.48 and the host range must be 192.168.10.49 to 192.168.10.62, remembering that the subnet and broadcast address cannot be used.
What is the valid host range of the 1st subnet of 172.16.0.0/17?
/17 tells us that the block size is 224-17 = 27 = 128. We are borrowing in the 3rd octet as bit 17 is in the 3rd octet. Our subnets are:-
172.16.0.0
172.16.128.0
The first subnet is 172.16.0.0 and the valid host range is 172.16.0.1 to 172.16.127.254. You must remember not to include the subnet address (172.16.0.0) and the broadcast address (172.16.127.255).
What is the valid host range of the 7th subnet of address 10.0.0.0/14?
The block size is 4, from 16 - 14 = 2 then 22 = 4. We are borrowing in the second octet so count in the block size from 0 seven times to get the seventh subnet.
The seventh subnet is 10.24.0.0. Our valid host range must be 10.24.0.1 to 10.27.255.254 again remebering not to include our subnet (10.24.0.0) and the broadcast address (10.27.255.255).
What if they give me the subnet mask in dotted decimal?
If you're lucky and they give you a mask in dotted decimal format then you should have an even easier time. All you need again is your block size.
Let's say they have given a mask of 255.255.255.248 and you wish to know the block size. Here's the technique:
1. Starting from the left of the mask find which is the first octet to NOT have 255 in it.
2. Subtract the number in that octet from 256 to get your block size (e.g. above it is 256 - 248 = block size of 8).
3. Count up from zero in your block size in the octet identified in step 1 as you have learned above (the example above would be in the last octet).
Another example is a mask of 255.255.192.0 - you would simply count up in 256 - 192 = 64 in the third octet.
One more example is 255.224.0.0 - block size is 256 - 224 = 32 in the second octet.
What other questions may they ask?
You may find they ask for how many bits you need to borrow for a certain amount of subnets, the subnet mask needed for a certain number of hosts, or the number of hosts per subnet. THESE ARE ALL EASY TO CALCULATE! All you need to remember is that you borrow bits for subnets and reserve bits for hosts.
There are two simple formulas:
Number of subnets = 2n where n is the number of bits borrowed
Number of hosts = 2(32 - n) - 2 where n is the number of bits in your subnet mask
Let's think of some questions. How many bits do you need to borrow to accommodate 6 subnets? No matter what address you are given the maths is still the same. The formula is 6 = 2n so you must find n which in this case is 3 as n = 2 gives only 4 subnets and n = 3 gives 8 subnets. Simply add n to your mask for your new subnet mask. For example, if you had a /24 address and you wanted 8 subnets then your mask will be 24 + 3 = /27.
What subnet mask should you use if you wanted 60 hosts per subnet? The formula is 60 = 2(32 - n) - 2 so you must find n which is 26. This is easy to find as you know that 26 - 2 = 62 so simply subtract 6 from 32 to get the 26. Therefore your mask is /26.
Lastly the number of hosts per subnet. How many hosts per subnet in the address 172.16.0.0/23? You have a /23 address therefore you formula is x = 2(32 - 23) - 2 = 29 - 2 = 510.
Another typical question they may ask will be giving you an IP address and mask and asking how many subnets and hosts there are from that address, for example:
Question: How many subnets and hosts per subnet can you get from the network 172.30.0.0/28?
From this you only need two pieces of information:
1. The default subnet mask of the address class.
2. The subnet mask in the question
Using the example above we know that:
1. The default subnet mask is /16 as the address given is a class B address
2. The subnet mask in the question is /28
The number of subnets = 2 ^ (subnet_mask_in_question - default_subnet_mask)
The number of hosts = (2 ^ (32 - subnet_mask_in_question)) - 2
For our example question the number of subnets = 2 ^ (28 - 16) = 2 ^ 12 = 4096 subnets.
The number of hosts = (2 ^ (32 - 28)) - 2 = (2 ^ 4) - 2 = 14 hosts per subnet
Let's use another address: 192.168.1.0/29
We know that:
1. The default subnet mask is /24 as the address given is a class C address
2. The subnet mask in the question is /29
The number of subnets = 2 ^ (29 - 24) = 2 ^ 5 = 32 subnets.
The number of hosts = (2 ^ (32 - 29)) - 2 = (2 ^ 3) - 2 = 6 hosts per subnet
Finally, let's use another address: 10.1.1.0/24
We know that:
1. The default subnet mask is /8 as the address given is a class A address
2. The subnet mask in the question is /24
The number of subnets = 2 ^ (24 - 8) = 2 ^ 16 = 65536 subnets.
The number of hosts = (2 ^ (32 - 24)) - 2 = (2 ^ 8) - 2 = 254 hosts per subnet
Easy isn't it?
What now?
Now it's time to go and pick up those books again and go straight to the practice questions, completely by-passing any of their techniques. Use my method and you will be laughing!
If you are unsure that you have the correct answers why not download a subnet calculator to double-check your answers? There is a great one by 3Com and can be downloaded from here.
Happy subnetting!
Posted byChris Bloomfield at 16:20 78 comments
Labels: best subnetting guide, block size, ccda, CCNA, ccnp, cidr, Cisco, easy, guide, ip, made, mask, Subnetting, VLSM
OSPF and NBMA Networks
Tuesday, 27 November 2007
Confused about which NBMA network type requires a DR/BDR or neighbours to be statically defined? Worry no longer..............................
If the keyword nonbroadcast is within the network type (i.e. ip ospf network non-broadcast, or ip ospf network point-to-multipoint non-broadcast) then neighbours must be defined.
If the keyword point is within the network type (i.e. ip ospf network point-to-point, ip ospf network point-to-multipoint, ip ospf network point-to-multipoint non-broadcast) then a DR/BDR is NOT elected.
You may see a question which has an output showing the network type as point-to-multipoint. It will then ask you to choose a couple of correct answers. From above we know the answer to be that DR/BDR are not elected and neighbours do not need to be statically defined.
HTH!
Posted byChris Bloomfield at 15:47 2 comments
Labels: bdr, broadcast, dr, frame relay, multipoint, nbma, non-broadcast, ospf, point
Route Summarization
Friday, 23 November 2007
Some people get really confused when it comes to route summarization, probably more so with the different names given to it:
Route Summarization
Supernetting
Aggregate Address
Summary Address
Actually, I get more confused typing out this thing as being English I want to replace the z in "summarization" with an s, but as it's Cisco I best keep the z in, lol. I also get this with "neighbor" versus "neighbour".
Anyway, I digress. The above terms all mean the same thing.
What is summarization?
The process of taking a range of IP addresses and advertising them in one address block. The most well-known summarization/supernet is the RFC1918 Class B Range. More commonly we know the range to be 172.16.0.0 - 172.31.255.255, however the supernet is 172.16.0.0/12. You see what has happened there? We've taken a range of addresses and squashed it into one advertisement.
What are the benefits of summarization?
Quite clearly, if we have just one address instead of lots of individual addresses then the routing table is going to be smaller. This in turn means that memory requirements are reduced.
The less obvious benefit is that summarization means you're tracking whether or not you're connected to some subnets of a summary, not the up/down state of every link. Thus when the link goes up or down, you don't have a flurry of traffic announcing the state change.*
How to summarize/supernet?
This is what you really want to know isn't it? Well it's dead simple.
The first method shows you the long way.
1. Starting from the left of the IP address, identify the first octet that has a change of address in it. For example, the Class B RFC1918 range, the IP address first changes in the second octet (i.e. 172.16.x.x - 172.31.x.x).
2. Write out the binary equivalent of the address up to and including the changing octet. So for example the range above is:
10101100.00010000 = 172.16
10101100.00010001 = 172.17
10101100.00010010 = 172.18
10101100.00010011 = 172.19
10101100.00010100 = 172.20
10101100.00010101 = 172.21
10101100.00010110 = 172.22
10101100.00010111 = 172.23
10101100.00011000 = 172.24
10101100.00011001 = 172.25
10101100.00011010 = 172.26
10101100.00011011 = 172.27
10101100.00011100 = 172.28
10101100.00011101 = 172.29
10101100.00011110 = 172.30
10101100.00011111 = 172.31
3. From this list, count from the left how many bits are the same in each address. If we look at it we see that the first 12 bits for each address is the same so that gives us our mask in slash notation. We therefore start at our first address 172.16.0.0 and append our mask so the summary address is 172.16.0.0/12.
Well that was quite simple. But can we be quicker? Yes we can is the good news, after all, you don't want to eat up time in the exam by writing out addresses in binary. So here goes:
1. How many subnets are in the range? The RFC1918 Class B range is 16 subnets.
2. What power of 2 equals our range? 16 subnets = 24 so the answer is four.
3. Subtract the figure from step 2 from the default mask of our address range. In this example our default mask is 16 so the mask after subtracting 4 is /12.
4. Add this mask to the first address in the range - 172.16.0.0/12 in this example
Quick, eh? This is how it works in my head, "mmmm, 16 addresses, 2 to the 4 is 16, mask is 16, minus 4 is 12, so summary address must be first address with /12 mask."
One last example:
Summarise the following:
192.168.0.0/24
192.168.1.0/24
192.168.2.0/24
192.168.3.0/24
There are 4 subnets. 2 to the power of 2 gives us 4 so default mask of 24, minus 2, gives us /22. Address is therefore 192.168.0.0/22.
More difficult supernetting question
There are, however, a few pitfalls with supernetting/summarization. Sometimes you may not be able to get all of the addresses into a supernet without wasting addresses. Experience with supernetting questions will help you to identify this. An example below shows you how this could happen:
You need to summarize the following range:
10.16.31.0/24
10.16.32.0/24
10.16.33.0/24
10.16.34.0/24
10.16.35.0/24
10.16.36.0/24
10.16.37.0/24
10.16.38.0/24
10.16.39.0/24
10.16.40.0/24
What summary address should you use? Well there's 10 subnets. 2 to the power of 3 only gives us 8 subnets which is too small so we need to look at 2 to the power of 4 which is 16. The problem is that if we count in 16s our addresses straddle two subnets: 10.16.16.0 to 10.16.31.255 and 10.16.32.0 to 10.16.47.255. We have the same problem if we use the power of 5 giving us a range of 32 addresses (10.16.31.0 is in a different subnet than the other addresses in the range). We therefore have to go out to 2 to the power of 6 = 64 in order to get all of our addresses in the range (i.e. 10.16.0.0 to 10.16.63.255). What a waste of address space!!
The best answer is the following:
Break the space down into three ranges. We can summarize 10.16.32.0 to 10.16.39.255 with 3 bits (i.e. there are 8 subnets and 2 to the power of 3 is 8). We simply leave the other two address as they are. We have therefore avoided any wasted address space.
If you are unsure that you have the correct answers why not download a subnet calculator to double-check your answers? There is a great one by 3Com and can be downloaded from here.
I hope this has helped you with route summarization.
Chris
*http://www.netcraftsmen.net/welcher/papers/ospf2.htm
Posted byChris Bloomfield at 09:43 80 comments
Labels: Aggregate, Route Summarization, Summarisation, Supernetting, VLSM
CCNA - Connecting devices
Wednesday, 21 November 2007

Don't worry about remembering which type of cable should be used when connecting alike or different devices. Use the simple diagram to the left and you won't go wrong!
Posted byChris Bloomfield at 14:50 6 comments
Labels: cable, cabling, CCNA, crossover, host, hub, layout, rollover, router, straight-through, switch
NAT in a Nutshell
Network Address Translation (NAT) and Port Address Translation (PAT)
NAT operates on a Cisco router, usually connecting two networks together, and translates the private (inside local) addresses in the internal network to public addresses (inside global) before packets are forwarded to another network.
As part of this functionality, you can configure NAT to advertise only one address for the entire network to the outside world. This effectively hides the internal network from the world, thus providing additional security.
In NAT terminology, the inside network is the set of networks that are subject to translation. The outside network refers to all other addresses. Usually these are valid addresses located on the Internet.
Cisco defines the following NAT terms:
- Inside local address: The IP address assigned to a host on the inside network. The address is likely not an IP address assigned by the NIC or service provider.
- Inside global address: A legitimate IP address assigned by the NIC or service provider that represents one or more inside local IP addresses to the outside world.
- Outside local address: The IP address of an outside host as it appears to the inside network. Not necessarily a legitimate address, it is allocated from an address space routable on the inside.
- Outside global address: The IP address assigned to a host on the outside network by the host owner. The address is allocated from a globally routable address or network space.
NAT has many different forms and can work in the following ways:
- Static NAT: Maps an unregistered IP address to a registered IP address on a one-to-one basis. Static NAT is particularly useful when a device needs to be accessible from outside the network.
- Dynamic NAT: Maps an unregistered IP address to a registered IP address from a group of registered IP addresses.
- Overloading: is a form of dynamic NAT that maps multiple unregistered IP addresses to a single registered IP address (many-to-one) by using different ports, known also as PAT.
PAT uses unique source port numbers on the inside global IP address to distinguish between translations. Because the port number is encoded in 16 bits, the total number of internal addresses that can be translated using NAT to one external address could theoretically be as many as 65,536 per IP address.
Configuring Static Translation
The ip nat inside source static command establishes static translation between an inside local address and an inside global address.
Router(config)#ip nat inside source static local-ip global-ip
To remove static translation use no ip nat inside source static
The ip nat inside command marks the interface as connected to the inside.
Router(config-if)#ip nat inside
The ip nat outside command marks the interface as connected to the outside.
Router(config-if)#ip nat outside
The complete process is below (variables in italics):
Router(config)#ip nat inside source static local-ip global-ip
Router(config)#interface type number
Router(config-if)#ip_address subnetmask
Router(config-if)#ip nat inside
Router(config-if)#interface type number
Router(config-if)#ip_address subnetmask
Router(config-if)#ip nat outside
Configuring Dynamic Translation
The ip nat pool command defines a pool of global addresses to be allocated as needed.
Router(config)#ip nat pool name start-ip end-ip {netmask netmask prefix-length prefix-length}
To remove dynamic translation use the no ip nat pool command.
The access-list access-list-number command defines a standard IP access list permitting those inside local addresses that are to be translated.
Router(config)#access-list access-list number permit source [source-wildcard]
The ip nat inside source command establishes dynamic source translation, specifying the access list defined in the prior step.
The complete process is shown below:
Router(config)#ip nat pool name start-ip end-ip {netmask netmask prefix-length prefix length}
Router(config)#access-list access-list-number permit source [source-wildcard]
Router(config)#ip nat inside source list access-list-number pool pool-name
Router(config)#interface type number
Router(config-if)#ip nat inside
Router(config-if)#interface type number
Router(config-if)#ip nat outside
Configuring Overloading (PAT)
The access-list access-list-number command defines a standard IP access list permitting those inside local addresses that are to be translated.
Router(config)#access-list access-list-number permit source source-wildcard
Enter the global no access-list access-list-number command to remove the access list.
The ip nat inside source list command establishes dynamic source translation, specifying the access list defined in the prior step.
Router(config)#ip nat inside source list access-list-number interface interface_type/number overload
It is the “overload” keyword that enables PAT.
The complete process is shown below:
Router(config)#access-list access-list-number permit source [source-wildcard]
Router(config)#ip nat inside source list access-list-number interface interface_type/number overload
Router(config)#interface type number
Router(config-if)#ip nat inside
Router(config-if)#interface type number
Router(config-if)#ip nat outside
Example:
Router(config)#access-list 1 permit 192.168.3.0 0.0.0.255
Router(config)#access-list 1 permit 192.168.4.0 0.0.0.255
Router(config)#ip inside nat source list 1 interface Serial0 overload
Router(config)#interface Ethernet0
Router(config-if)#ip address 192.168.3.1 255.255.255.0
Router(config-if)#ip nat inside
Router(config)#interface Ethernet1
Router(config-if)#ip address 192.168.4.1 255.255.255.0
Router(config-if)#ip nat inside
Router(config)#interface Serial0
Router(config-if)#ip address 172.17.38.1 255.255.255.0
Router(config-if)#ip nat outside
Clearing the NAT translation table
After you have configured NAT, verify that it is operating as expected. You can do this by using the clear and show commands.
Router#clear ip nat translation *
This clears all dynamic address translation entries from the NAT translation table, the * is a wildcard meaning "all".
Router#clear ip nat translation inside global-ip local-ip [outside local-ip global-ip]
This clears a simple dynamic translation entry containing an inside translation, or both inside and outside translation.
Router#clear ip nat translation outside local-ip global-ip
This clears a simple dynamic translation entry containing an outside translation.
Router#clear ip nat translation protocol inside global-ip global-port local-ip local-port [outside local-ip local-port, global-ip global-port]
This clears an extended dynamic translation entry.
Displaying NAT information
You can display translation information by performing one of the following tasks in EXEC mode.
Router#show ip nat translations – displays active translations
Router#show ip nat statistics – displays translation statistics.
Troubleshooting the NAT and PAT Configuration
Use Router#debug ip nat
Posted byChris Bloomfield at 13:29 5 comments
Labels: CCNA, Cisco, Dynamic, Inside Global, Inside Local, NAT, Outside Global, Outside Local, PAT, Static, Subnetting


